This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
TL;DR
Subdomain takeover is not a new threat, but in today’s AI-driven cyber landscape, the velocity and scale at which these attacks can be launched is unprecedented. This blog explores a lesser-known variant of subdomain takeover involving standalone, non-fully qualified CNAME records. A technical nuance with major implications. It underscores how this seemingly small misconfiguration can become a high-leverage vector for phishing, malware deployment, and session hijacking. For CISOs and cybersecurity leaders, this is a call to close yet another silent gap in the digital attack surface that traditional tools simply don’t see.
Understanding Subdomain Takeover
Modern enterprises often rely on complex web architectures, with thousands of domains and subdomains distributed across cloud platforms, SaaS vendors, and internal systems. These subdomains are frequently tied to external services using DNS CNAME records. A typical example:
sub.example.com CNAME sub.azurewebsites.net
The risk begins when the underlying cloud service (e.g., the Azure web app) is deleted or decommissioned, but the DNS entry remains. This orphaned CNAME now points to a non-existent resource. AI-powered reconnaissance bots (AI.Attackers) scan for these forgotten DNS records at scale, claim the vacant resource names, and instantly hijack the subdomain.
To any user visiting sub.example.com, the hijacked subdomain behaves normally. But behind the scenes, it now serves attacker-controlled infrastructure. These takeovers are low-noise, high-impact, and often completely invisible to standard detection mechanisms.
Subdomain takeovers are not merely theoretical constructs but real-world tactics used by adversaries to exploit DNS hygiene lapses. Once a subdomain is hijacked, attackers can impersonate internal services, inject malicious scripts, intercept sensitive information, and deceive users by mimicking the organization's digital footprint. For a CISO, this transforms from a technical vulnerability to a strategic liability that affects brand trust, customer security, and compliance obligations.
Organizations with fragmented DNS management practices are particularly at risk. In many cases, subdomains are provisioned rapidly during development sprints, proof-of-concept rollouts, or short-lived marketing campaigns. These initiatives often bypass the formal IT asset inventory process and result in shadow infrastructure. DNS records left pointing to resources long since deprecated. These forgotten links become prime hunting ground for AI.Attackers.
Enter the Overlooked Variant: Standalone Host CNAMEs
Now consider a CNAME record that does not point to a fully-qualified domain (FQDN), but to a single-label hostname:
In traditional DNS setups, this configuration is ambiguous. However, in enterprise environments that utilize Microsoft Active Directory (AD) with DNS suffix search lists or domain search ordering, name resolution behaviour includes appending suffixes to incomplete queries. This means the DNS resolver will attempt the following resolution steps:
- Resolve uio2.example.com (using the internal domain suffix)
- If unsuccessful, fall back to uio2.com (assuming it's a global TLD)
This behaviour relies on the system's DNS resolver settings, specifically:
- DNS Suffix Search List configured either via Group Policy or manually
- Primary DNS Suffix (defined in system properties)
- Devolution logic in Windows DNS client, which attempts to trim domain names step by step
In environments where users or systems have AD-joined configurations and operate under domains like sub.corp.com, the resolution logic can lead to cross-domain traffic redirection. If uio2.com is registered and active, any user or application relying on the ambiguous host CNAME (like uio2) will silently redirect to an attacker-controlled server.
Critically, this does not require the attacker to compromise the organization directly. If the user’s DNS resolution steps include checking external domains (as a fallback), the attacker simply needs to:
- Find subdomains with a CNAME of a single word
- Register the single word host as a domain with a high impact TLD domain (e.g., host.com)
- Stand up infrastructure that will be served to victims.
The attacker’s registration of host.com doesn’t just impact the organization with the forgotten subdomain, but also other users within any domain structure that appends matching suffixes in resolution. For example:
- A subdomain misconfigured as CNAME uio2 in example.com
- A user in a different org, example-2.com, has their AD DNS policy try uio2.example-2.com then uio2.com
This becomes a supply-chain-like risk pattern. The impact spreads across federated, trusted, or same-TLD organizational structures. As a result, this vulnerability is not just isolated to one org’s hygiene but can propagate due to shared domain behavior patterns.
This is not theoretical. It happens. With AI-driven reconnaissance tooling, it's happening more frequently. The wide availability of open-source enumeration tools and scanners (like Censys or Shodan) means adversaries can identify these errors quickly and at scale.
How to Check if This Applies in Your Organization
Configuring and Auditing DNS Suffix Search Lists via Group Policy
In Active Directory environments, DNS suffix search behavior is centrally controlled by domain administrators. It determines how client machines resolve single-label hostnames, which is directly relevant to the host-based CNAME takeover scenario.
To audit and configure this behavior, domain admins should:
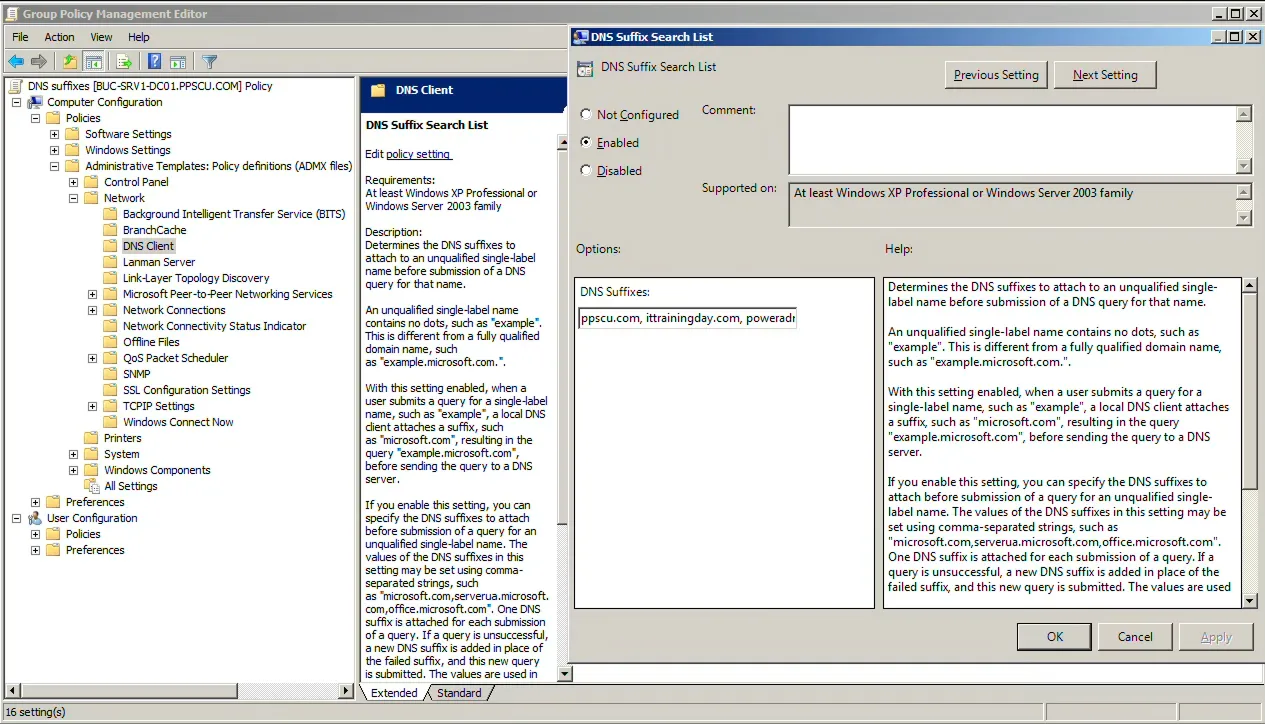
- Open the Group Policy Management Console (GPMC):
Navigate to: Computer Configuration → Policies → Administrative Templates → Network → DNS Client
- Edit the “DNS Suffix Search List” policy:
- Set the policy to Enabled
- Specify a comma-separated list of internal suffixes (e.g., corp.example.com,example.com) This defines which DNS suffixes will be automatically appended when clients attempt to resolve single-label hostnames.
- Apply the Group Policy:
Verifying DNS Suffix Behavior on Client Machines
While users cannot modify the policy if it is applied via GPO, they can verify whether suffix completion is active on their system:
- Open Command Prompt
- Run: nslookup <a single label host>
- If the output shows the resolver attempting to resolve host.<TLD>, then suffix search is active — either via GPO, DNS, or local configuration.
Mitigation Best Practices
- Avoid using single-label CNAMEs in your DNS zones. Always use fully qualified domain names (FQDNs).
- Limit the suffix search list to trusted, internal domains only.
- Regularly audit subdomains with CNAMEs pointing to single-label hosts, especially legacy records.
- Monitor for DNS queries to external domains that match known internal hostnames.
Attack flow
A user in Company A’s office attempts to access a legitimate subdomain of Company B via the company’s DNS server, but is instead directed to a malicious website controlled by an attacker.
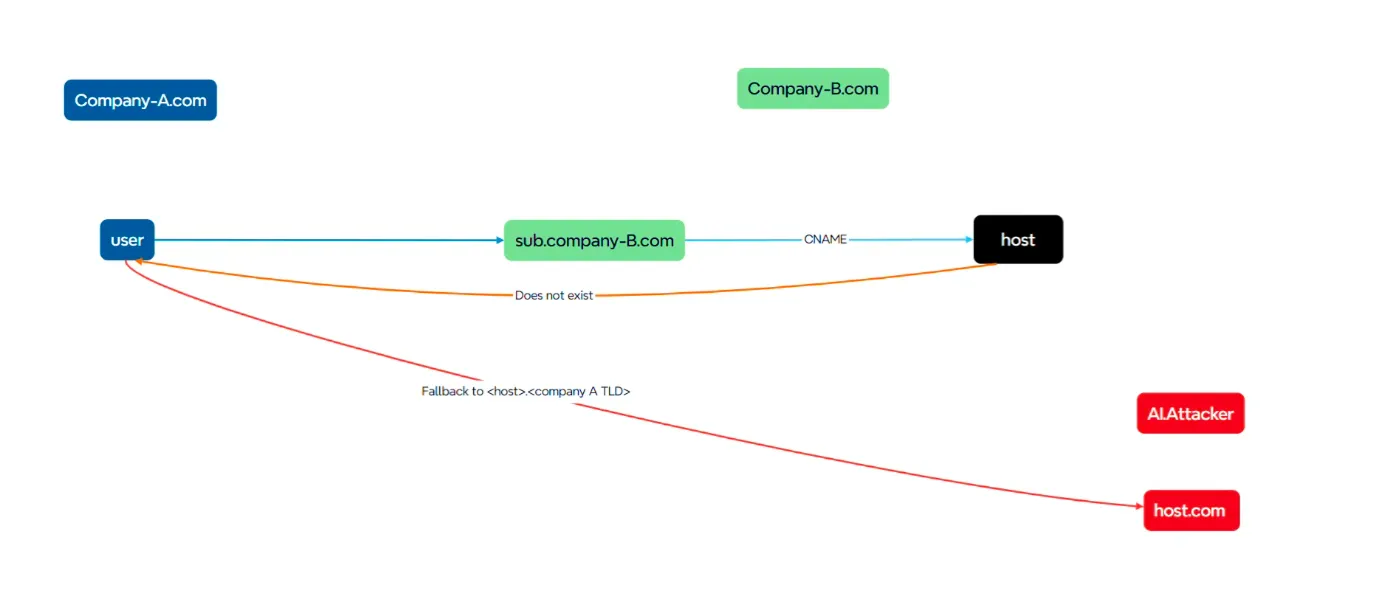
AI.Attacker side
An automated system identifies and takes over abandoned or misconfigured subdomains pointing to external hosts — often completing the takeover in seconds.

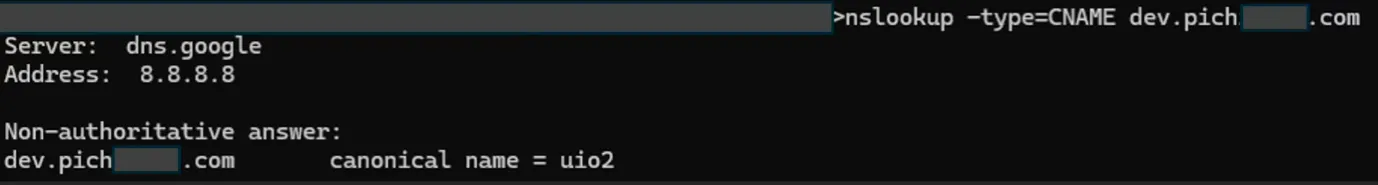
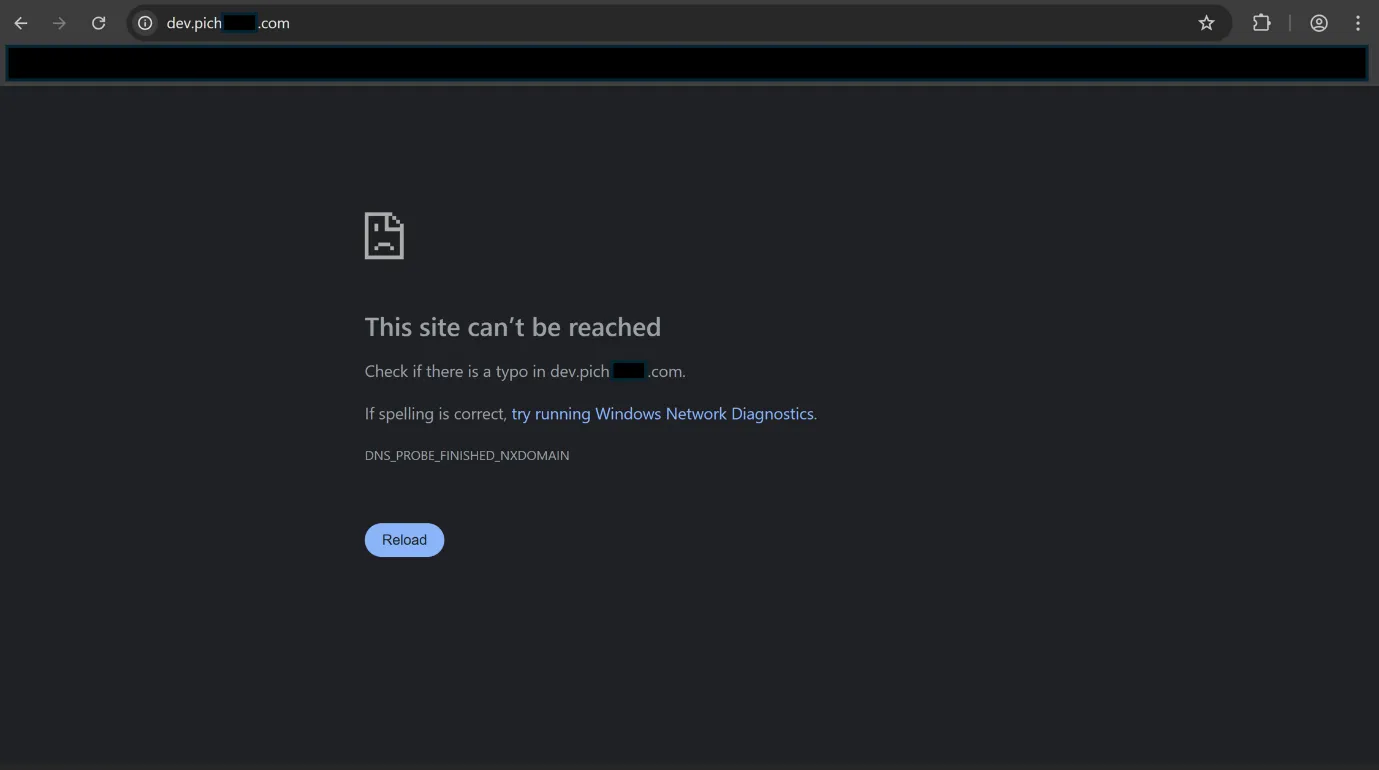
Client side - before takeover
The user tries to visit dev.pitch*****.com, but subdomain does not exist.
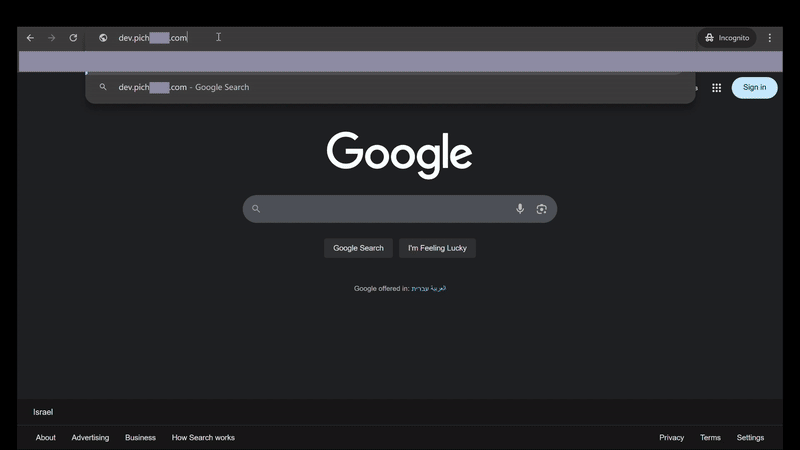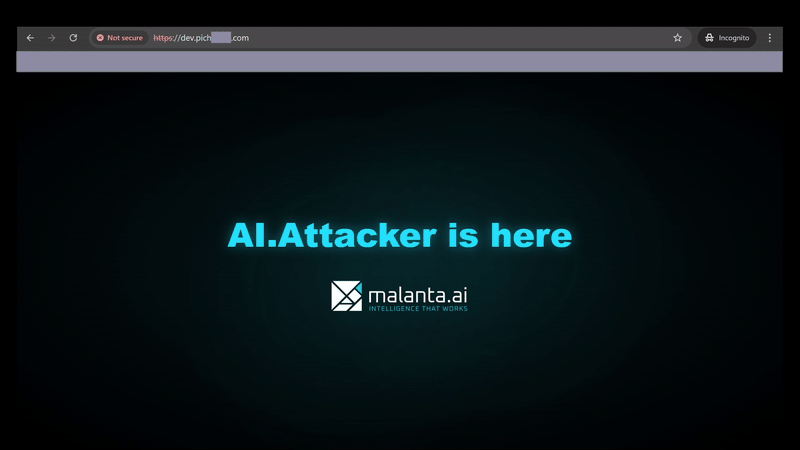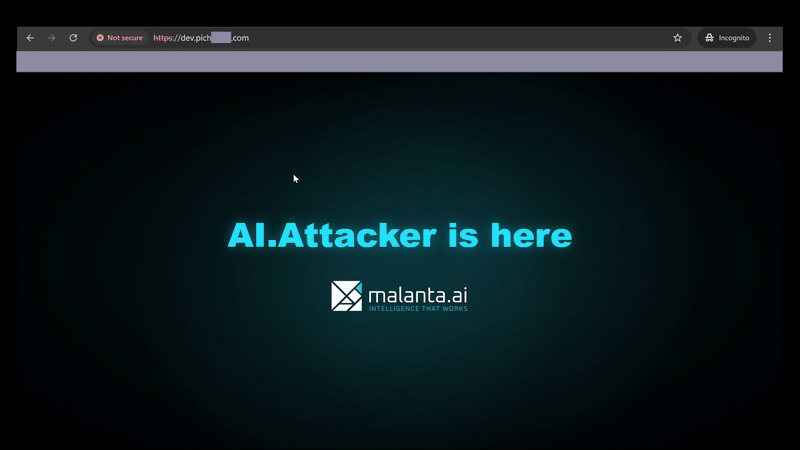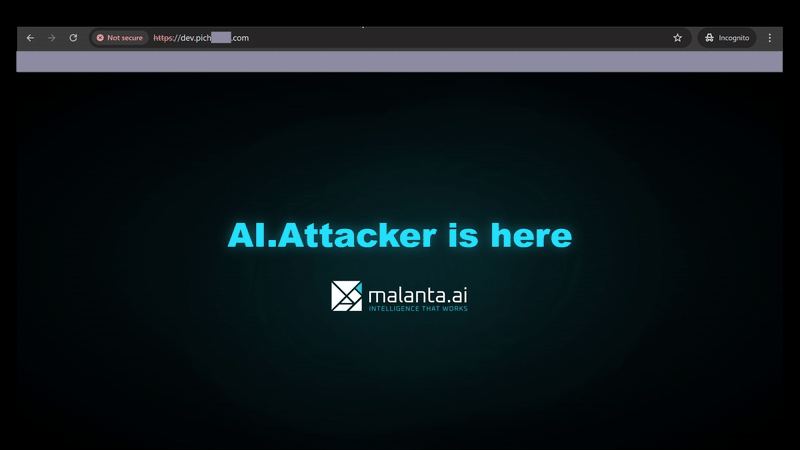
Client side - after takeover
The user tries to visit dev.pitch*****.com (a subdomain of Company B), but is unknowingly redirected to a malicious domain. This can lead to malware infection, cookie theft, or phishing.
Under the Hood - Wireshark Capture
Network traffic shows that the user’s request for dev.pitch*****.com resolves to an attacker-controlled domain (uio2.com) via Company A’s DNS server.
.webp)
Why This Is Invisible to Traditional Security Stacks
Subdomain takeovers, especially those using external or ambiguous CNAME records, operate entirely outside the perimeter of the organization. The attacker hosts infrastructure on public cloud providers. DNS is a public-facing, unauthenticated vector. The hijacked domain appears completely legitimate, even to security tools.
- EDRs? They won’t trigger. This is not organization’s endpoint.
- SIEMs? No unusual logs. It is in the cloud provider logs you don’t control.
- Firewalls? Traffic is encrypted and appears to go to example.com.
- DLP? No data exfiltration signature gets triggered unless user behavior is linked.
This is the perfect crime: nothing within the organization's infrastructure is directly touched, yet user trust and security posture are completely undermined.
Worse, the response is delayed. Organizations often discover these attacks only after users report phishing emails that look too real, or after threat hunting teams stumble upon domain anomalies. The cost of being reactive is immense: reputational damage, compliance failures, and user compromise.
The disconnect between DNS configurations and active asset monitoring is a systemic flaw. Many DNS changes are executed manually or in silos, detached from the central inventory or security operations. Without a real-time feedback loop between DNS management and exposure detection, attackers will always be a step ahead
How AI.Attackers Weaponize This Faster Than Ever
AI.Attackers operate differently than traditional attackers. They:
- Scan thousands of domains for dangling or ambiguous CNAME records
- Autonomously claim cloud resources on Azure, AWS, GitHub Pages etc.
- Deploy phishing pages that look identical to corporate login screens
- Harvest session tokens using cookie misconfiguration
- Exploit domain trust to bypass email security and MFA
- Use AI-generated content to personalize lures and deceive users more effectively
The shift is in speed and autonomy. What took hours or days of manual reconnaissance now happens in seconds. Tools powered by large language models (LLMs) and real-time feedback loops adjust attacks on the fly, generating phishing kits, deploying content, and adapting based on click-through rates.
AI.Attackers also benefit from economies of scale. With AI-powered orchestration platforms, a single adversary can manage hundreds of takeover campaigns simultaneously, each adapted in real time based on user interaction data. Attack kits are increasingly modular, enabling adversaries to mix-and-match components like redirection logic, CAPTCHA bypasses, and C2 channels.
Business Risk: What Happens If This Is Exploited?
If an attacker gains control of a subdomain via CNAME hijacking, the implications are severe:
- Credential Harvesting: Users input corporate credentials into fake login screens
- Malware Hosting: Drive-by downloads or payload drops happen silently
- Command and Control (C2): Hijacked subdomains act as beacons for exfiltrating data
- Session Hijacking: Over-scoped cookies (Domain=.example.com) allow access to all sibling subdomains
- Data Theft or Ransomware Deployment: Via social engineering or session replay
The attack is not just technical; it is reputational. Victims trust domains like support.example.com or login.example.com. Any compromise here damages the brand irreparably. Moreover, breaches via subdomain takeover can trigger regulatory scrutiny under laws like GDPR, HIPAA, and CCPA.
In third-party ecosystems (e.g., banking apps using partner APIs), such takeovers can have cascading impacts. Customers, partners, and regulators will ask the hardest question: Why wasn't this discovered sooner?
Legal and contractual implications also emerge. Many organizations have obligations to safeguard customer data even in third-party contexts. A hijacked subdomain can be interpreted as negligence in cyber hygiene, opening the door for legal liability and civil penalties.
The Strategic Flaw: Blind Spots in Asset Management
CISOs often believe their digital footprint is mapped and monitored. But ask this:
- Do you know every subdomain still pointing to a deprecated cloud service?
- Are your DNS records being monitored for ambiguity or standalone values?
- Can you detect attacker infrastructure mimicking your subdomain structure?
- Are cookie policies scoped to least privilege?
If the answer is “no” or “I think so,” there is risk. In today’s environment, partial visibility is the same as no visibility.
Too many organizations still rely on asset inventories built quarterly or annually. The cloud does not move on quarterly cycles. Attackers don’t wait for your patch management window. You are fighting adversaries who operate on machine time.
Security leadership must treat asset visibility as a live, evolving practice. This means deploying tools and processes that track infrastructure changes in real time, not just periodically. Asset intelligence must be tightly integrated with exposure validation workflows to close the time gap between risk emergence and mitigation.
Action Plan for CISOs and Security Leaders
- Audit Your DNS Records
- Search for CNAMEs that point to deprecated or generic single word values (e.g., host, dev, test)
- Eliminate orphaned records with no active backend
- Use automation to revalidate DNS health regularly
- Monitor for External DNS Activity
- Use threat intel feeds to detect registrations of suspicious lookalike subdomains
- Track external infrastructure that mimics your DNS or SSL fingerprint
- Integrate DNS monitoring into your threat modeling program
- Implement Pre-Attack Prevention
- Move beyond passive inventory
- Correlate adversial resources and your weak spots
- Prevent what’s about to happen based on urgency. Not priority.
- Enforce DNS and Cookie Governance
- Define policy for scoping cookies by subdomain (avoid wildcard scoping)
- Prohibit non-FQDN CNAME entries in DNS zone files
- Review infrastructure teardown processes to ensure DNS entries are removed
- Educate Internal Stakeholders
- Alert marketing and dev teams about the risks of short-lived cloud projects
- Create awareness of what DNS records and SSL certificates imply
- Emphasize the need for proper offboarding processes
- Simulate Takeovers in Red Team Exercises
- Task red teams to identify exploitable subdomains
- Use their findings to test detection and response readiness
- Continuously iterate based on lessons learned
Final Word: Invisible, Fast, and Preventable
What makes this threat so dangerous is not its complexity, but its invisibility and speed. A dangling CNAME with a single-word host can look like a trivial config error. But in the hands of an AI.Attacker, it becomes a doorway.
And it doesn’t need to breach your firewall. It doesn’t trip your EDR. It doesn’t even touch your infrastructure.
But it breaches trust. It weaponizes what you forgot. And it does so before your team even knows what happened.
The only defense is proactive visibility. Not just of assets, but of how attackers see them. Not just of alerts, but of adversarial behavior. This is the shift from reactive defense to real security.










